Backstory, history of these types of attacks:
Hackers have found ways to impersonate any app that is on your browser, down to the code itself. A common practice in impersonating was to mock up a site similar to the one they’re trying to make you think is legit, or they take a screenshot and hope you dont notice the subtile differences between their modified screenshot, and a real popup from your actual computer.
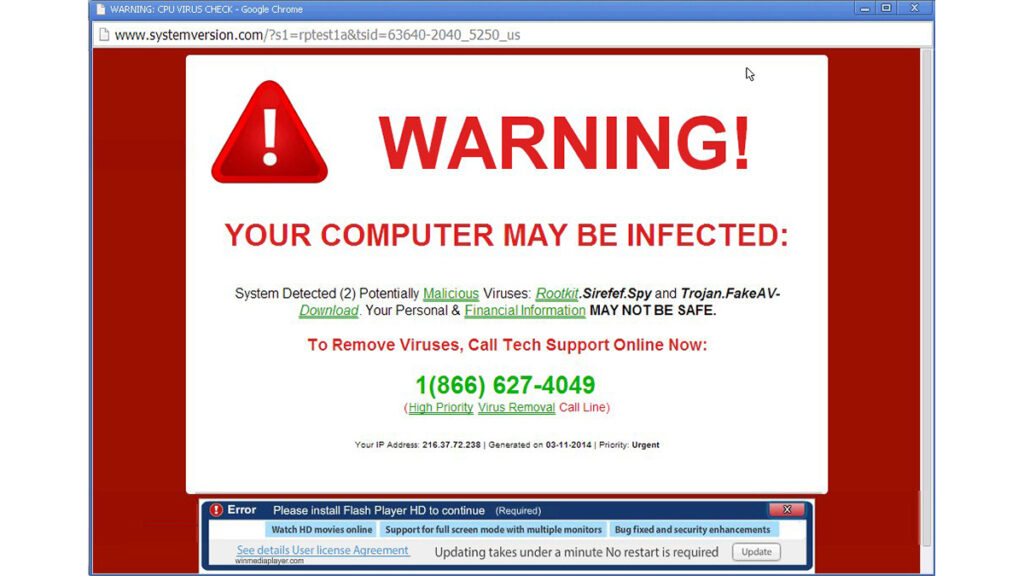

Pictured above was the old school way, still pretty common.
Modern Adaptations of that style attack:
But now, imagine instead of doing that, you just dynamically look at what plugins are running on the system and make your own modified copy of it, and point a few things back to you instead of where they’re supposed to go.
“When users click on what appears to be their password manager, they’re actually interacting with the malicious extension, which captures their master credentials and secret keys before seamlessly returning control to the legitimate extension.
Cyber Security News
This attack is particularly concerning as it exploits legitimate Chrome functionality and uses permissions classified as medium risk, making it difficult to detect through standard security measures.
The APIs used – activeTab, scripting, and chrome.management – are commonly used by legitimate extensions, allowing the malicious code to blend in with normal browser operations.”
Put another way, it looks at what info your trusted extension is using, it copies it and sends it to the hackers, then the real extension pops up afterward.
steps to minimize this being a possibility- use a version of chromium or Firefox that isn’t ran by Google or Mozilla. Ungoogled is a good google alternative, and Zen is a good Firefox alternative. This vulnerability doesn’t affect Firefox and Firefox forks, but Firefox has had their own controversies recently that are not making people happy.
How is tech news like this relevant to politics?
Great question! In this day an age, the people in control, who are almost always billionaire capitalists, and politicians in bed with billionaires, they want all of your data. they want everything they can get. they will find out everything they can whether obtained legally or illegally. If you dont think the NSA buys and trades with stolen / hacked data, to further possibly use against you, the activist who wants to dismantle the state as it’s running today, – your best course of action is to protect yourself from data breaches, spying on, getting phished, the whole 9 yards. it’s why they say “dont bring your phone to a protest” – because they can filter out all phones within X yards of X protest location, and then they immediately have a list of about 4000 people instead of 10,000,000 potential people to comb through. if you want to be an activist, you MUST keep your ear to the ground on cybersecurity, or else you’ll get swept up like the leaves in the wind. And yes, you have everything to hide, activist or not. Dont willingly or ignorantly give your data away.